The DeFi ecosystem has mutated from an Ethereum-centric ecosystem to a multichain paradigm. To accommodate this new paradigm, many bridge solutions have emerged to transfer funds between blockchains. However, these can be prime targets for hackers. The Harmony blockchain learned this the hard way with the hack of its Horizon bridge.

100 million stolen from Harmony’s Horizon Bridge
Harmony is a smart contract blockchain called EVM-compatible. For the sake of interoperability with the rest of DeFi, Harmony has deployed its own bridge solution called Horizon.
In practice, Harmony has two bridges. We have the Horizon bridge which allows to link its blockchain to the Ethereum (ETH) and BNB Smart Chain (BNB) blockchains. As well as another bridge to connect Harmony to the Bitcoin (BTC) network.
Read more about : More than $600 million stolen from the Ronin network (Axie Infinity).
Early this morning, the Harmony teams warned the community that their Horizon bridge had been the target of a hack. In total, 592 WBTC have been stolen by the attacker, which is more than 100 million dollars at the current price.
Fortunately, this attack was restricted to the Horizon bridge and apparently did not impact the Bitcoin bridge.
“Note that this does not impact the untrusted BTC bridge; its funds and assets stored in decentralized vaults are safe for now.”
Teams quickly paused the Horizon Bridge in order to limit the damage. They also said they have begun “working with national authorities and forensic specialists” in an effort to identify the perpetrator of the attack.
How do these bridges work?
Before going into the details of the attack, let’s look at how these famous bridges work.
In practice, they work thanks to a set of smart contracts deployed on the various blockchains to be linked.
Thus, here are the steps performed when a user wants to send funds from Ethereum to Harmony:
°The user will deposit funds on the bridge smart contract deployed on Ethereum.
°A validation committee will then verify the existence of the deposit on Ethereum and block the funds on the contract.
°Once the funds are blocked on the contract, the same amount of tokens will be issued. These issued tokens are so-called tokenized tokens, which allow to represent a token that is not native to the Harmony blockchain.
As a result, the smart contracts deployed on both sides of the bridge hold large amounts of tokens. This makes these contracts prime targets for hackers of all stripes.
How the Horizon Bridge hack was carried out
For now, little information has been shared by Harmony’s teams vis-à-vis the Horizon hack. However, since the blockchain is a public ledger, many cyber investigators have been looking into the matter.
Thus, the @RugDocIO teams have conducted the investigation and published their findings in a thread on Twitter.
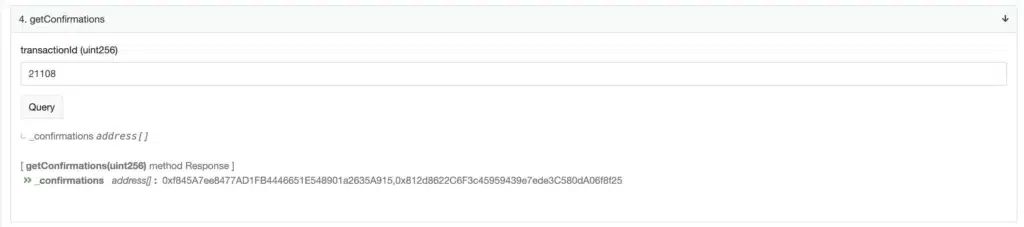
After investigation, they suspect the track of private key compromise. Indeed, the Horizon Bridge smart contract is controlled by a multi-signature or 5-party multisig wallet.
In practice, a multi-signature wallet is controlled by a defined number of addresses, belonging to different people.
However, to sign a transaction, the Horizon Bridge contract only required the approval of 2 of the 5 addresses that make up the multisig.
So, when looking more closely at the transaction that allowed the Horizon hack, @RugDocIO’s teams noticed that it had been signed by 2 of the 5 wallets of the multisig.
Two theories are then possible:
°It is an inside job, in which 2 of the multisig holders decided to steal the funds (unlikely theory).
°The two addresses used to sign the hack transaction were compromised and their original owners lost control of them (the most likely theory).
Subsequently, Harmony’s teams modified the rules of Horizon’s smart contract so that it requires at least 4 addresses of the multisig to sign a transaction.
The Harmony teams will probably try to contact the attacker in order to negotiate a return of the funds in exchange of a reward. It remains to be seen if the attacker will be inclined to return the funds, or if he will prefer to keep the money at the risk of being found by the law enforcement.




