In 2016, only a few months after the birth of the Ethereum blockchain, a decentralized autonomous organization was created.
Entitled The DAO, this organization was intended to fund the development of Ethereum and its ecosystem, in the manner of a venture capital fund. Unfortunately, it was soon the target of an attack, which has now become historical in the Ethereum ecosystem.
After years of ignorance, it seems that the identity of the DAO hacker has finally been revealed.
History of the DAO hack
Before we get into the details of the hacker’s identity, let’s take a look back together at this story that has forever marked the development of Ethereum.
It is 2016, the Ethereum blockchain was launched a few months before. However, this one lacks funds to finance its development and that of its ecosystem of smart contracts, then revolutionary.
This is how developers came up with the idea of developing a decentralized autonomous organization (DAO) working as a venture capital fund. This was born in April 2016 and was accompanied by the sale of DAO tokens in exchange for Ethers.

However, this sale never reached its end. Indeed, after more than 11,000 investors participated in the sale, a malicious hacker managed to exploit a flaw in the DAO’s smart contract.
As a result, the attacker managed to steal 3.6 million ETH, or about $50 million at the time. This brings the total loot from the now defunct DAO to $9.8 billion.
For comparison, those 3.6 million ETH represented at that time approximately 5% of the total supply of ETH tokens in circulation. This hack was a hecatomb for the Ethereum ecosystem and its community, which had to react quickly.
Reimbursement, dissension and fork
Following the attack, part of the Ethereum community campaigned for a fork to return the funds to the injured users. However, this proposal was far from being unanimous.
As a result, Ethereum was divided into two clans, the pro-fork and the anti-fork. On the one hand, the pro-fork actually performed the fork in order to reimburse the users victims of the hack, this new chain is none other than the Ethereum chain (ETH) as we know it now.
On the other side, the anti-fork decided to continue to mine and exploit the chain on which the attack had taken place. This one will now be called “Ethereum Classic” (ETC).
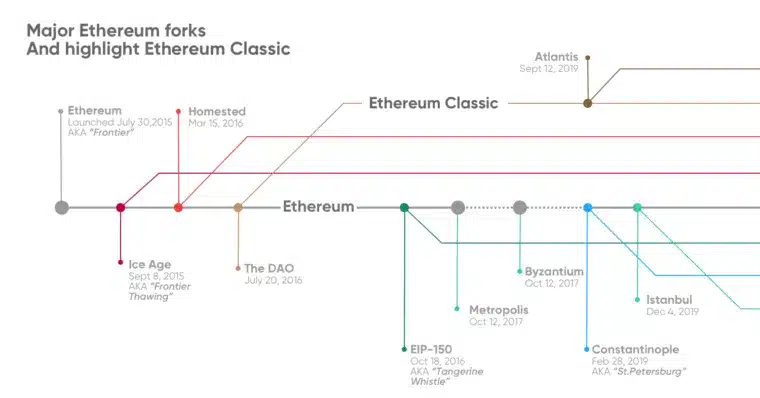
Despite the debates generated by this attack and the dissension it caused, the identity of the attacker remained a mystery.
Rebound on the identity of the hacker of The DAO
More than 6 years after the fact, the Ethereum network has recovered from this first attack. Since then, attacks like the DAO have unfortunately been repeated.
However, when no one expected it, journalist and podcast host Laura Shin dropped an unprecedented bombshell on the ecosystem by announcing she knew the identity of the DAO hacker.
According to information published in the highly reputable Forbes Magazine, the attacker would be none other than Toby Hoenisch, a 36-year-old Austrian developer expatriated in Singapore.
Obviously, Toby Hoenisch is not unknown to the crypto ecosystem. Indeed, he is the CEO and co-founder of the TenX project. As a reminder, TenX was a project wishing to democratize crypto bank cards during the 2017/2018 bull run.

“In 2016, he identified technical vulnerabilities in the DAO early on and may have decided to strike after concluding that his warnings were not taken seriously enough by the creators of the DAO,” Laura Shin explains in her article.
In the article, Shin explains that she tracked down the hacker using a “powerful, previously secret forensic analysis tool from crypto-currency tracking company Chainalysis.”
Toby Hoenisch denies it
On his side, Toby Hoenisch denies in block this version of the facts. Thus, Laura Shin would have tried to confront him with her findings by transmitting him the fruit of her research. However, this one answered only that its “declaration and conclusion are factually inaccurate”. Thereafter, Hoenisch never followed up on Laura Shin’s repeated messages.
Nevertheless, several elements seem to point in her direction. For example, the attacker made several attempts to launder funds, leaving behind traces. Among the attempts, the attacker used the anonymous crypto currency Grin. Unfortunately for Hoenisch, the Grin funds were withdrawn on a node called grin.toby.ai
In parallel, the IP address of this node also hosted two Lightning Network nodes, ln.toby.ai and lnd.ln.toby.ai.
There is no doubt that this story is just beginning. Indeed, it is highly likely that these revelations will have significant implications for the ecosystem. At the same time, several other investigations, such as the one conducted by the American SEC, could well benefit from this new information.




