How a blockchain works in simple terms
What is a blockchain? When we talk about a blockchain, it is usually about cryptocurrencies or NFTs. But how does a blockchain work to begin with, is it a program? A network?
To keep things simple, a blockchain is a series of blocks that are immutably linked; the information contained in these blocks is inscribed forever and cannot be altered, the blocks are connected and form a network in the form of nods. Security is paramount in blockchains as it is what gives them credibility. The information being written has to go through a series of trials and be certified by several actors in order to be included in the blockchain. It’s at this stage that a double-spending attack can occur.
When a new block is created, multiple operations are logged in it, such as the transfer of cryptocurrencies or the deployment of a smart contract for instance. Each digital operation is verified by third parties who are individuals and companies that use a cryptographic algorithm in order to ensure that the transaction is valid and devoid of any fraudulent element. The actors at play come to an agreement about the creation of a block through what we call a consensus algorithm.
Double-spending attacks in details
What is a double-spending attack then? This term is used when a user attempts to spend the same cryptocurrency twice. This type of attack happens at the moment a block is created.
For example, an individual that owns 1 Bitcoin and wishes to exchange it for both USDT and Ethereum at the same time should not be able to do so. Their Bitcoin can only be spent once in full. A double-spending attack would allow this user to use the same Bitcoin twice. Rest assured, this type of attack has never occurred on the Bitcoin blockchain.
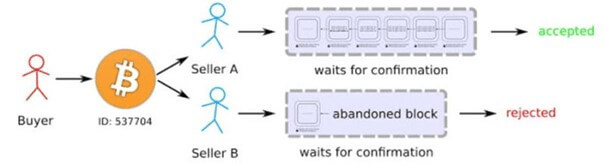
It is sometimes possible for the initiation of a double-spending attack to be made by accident during the creation of a block. When a block is being generated, it is expected that several actors compete during the creation process. As a consequence, the same Bitcoin can find itself in two different blocks. Nevertheless, only one block will be chosen and definitely logged in the blockchain; the longest one. This Bitcoin will therefore only be spent once.
The risks posed by a double-spending attack on a blockchain
What are the risks involved in a double-spending attack? This is one of the most dangerous attacks possible on a blockchain, comparable to a 51% attack for example. A double-spending attack can cause a cryptocurrency to be artificially multiplied while skewing the register of a blockchain, thereby jeopardizing its credibility.
Credibility is essential to a blockchain because if a double-spending attack is proven to have occurred on it in the past, we can infer that there are risks for such an attack to happen again. Moreover, every block that was built since the attack is considered to be “corrupt” and the blockchain is therefore betraying its own basic security principle.
All cryptocurrencies linked to this blockchain will then face a collapse of their values due to the existence of such a risk.
The ways to protect a blockchain against double-spending attacks
There are ways to protect yourself against double-spending attacks on a blockchain. Many methods and analyses are possible, but they will depend on your place in this blockchain: are you a user or a developer?
If you read this article as a blockchain developer, you will need to reinforce the cryptography of your validation algorithm in order to make a double-spending attack more complex to realize.
If you read this article as a user of a blockchain, you will mainly need to beware of small or recent blockchains. Indeed, it is far less likely for a double-spending attack to occur on the Bitcoin or Ethereum blockchain. However, if you are among the first users of a new blockchain, exercise caution regarding its inner workings and take the time to analyze them. If you can, use websites like etherscan.io for the new blockchain you have an interest in. Such a website will allow you to monitor the series of blocks and their content in order to ensure their conformity with the network and avoid attacks. We also recommend the use of a website like BlockExplorer to learn more about the use of a new blockchain.
Now that you know what a double-spending attack on a blockchain is, how to identify it, and protect yourself against it, you have one more string to your bow!
